 openldap配置自助修改密码
openldap配置自助修改密码
一般情况下,我们给先入职同学创建账户的时候,都会设置一个统一的账号,然后再由该同学自助修改密码,那么,就需要部署一个自助修改密码的服务,这里采用docker方式部署,简单便捷。
cat docker-compose.yml
version: '2'
services:
ssp-app:
image: registry.cn-hangzhou.aliyuncs.com/eryajf/self-service-password
container_name: ssp-app
volumes:
- ./data/:/www/ssp
- ./logs/:/www/logs
ports:
- 8888:80
environment:
- VIRTUAL_HOST=http://10.3.0.42
- VIRTUAL_NETWORK=nginx-proxy
- LETSENCRYPT_HOST=10.3.0.42
- LETSENCRYPT_EMAIL=Linuxlql@163.com
- LDAP_SERVER=ldap://10.3.0.42:389
- LDAP_STARTTLS=false
- LDAP_BINDDN=cn=admin,dc=eryajf,dc=net
- LDAP_BINDPASS=eryajf@456
- LDAP_BASE_SEARCH=ou=People,dc=eryajf,dc=net
- LDAP_LOGIN_ATTRIBUTE=uid
- LDAP_FULLNAME_ATTRIBUTE=cn
# Active Directory mode
# true: use unicodePwd as password field
# false: LDAPv3 standard behavior
- ADMODE=false
# Force account unlock when password is changed
- AD_OPT_FORCE_UNLOCK=false
# Force user change password at next login
- AD_OPT_FORCE_PWD_CHANGE=false
# Allow user with expired password to change password
- AD_OPT_CHANGE_EXPIRED_PASSWORD=false
# Samba mode
# true: update sambaNTpassword and sambaPwdLastSet attributes too
# false: just update the password
- SAMBA_MODE=false
# Shadow options - require shadowAccount objectClass
# Update shadowLastChange
- SHADOW_OPT_UPDATE_SHADOWLASTCHANGE=false
# Hash mechanism for password:
# SSHA
# SHA
# SMD5
# MD5
# CRYPT
# clear (the default)
# auto (will check the hash of current password)
# This option is not used with ad_mode = true
- PASSWORD_HASH=SHA
# Local password policy
# This is applied before directory password policy
# Minimal length
- PASSWORD_MIN_LENGTH=6
# Maximal length
- PASSWORD_MAX_LENGTH=30
# Minimal lower characters
- PASSWORD_MIN_LOWERCASE=2
# Minimal upper characters
- PASSWORD_MIN_UPPERCASE=1
# Minimal digit characters
- PASSWORD_MIN_DIGIT=1
# Minimal special characters
- PASSWORD_MIN_SPECIAL=0
# Dont reuse the same password as currently
- PASSWORD_NO_REUSE=true
# Show policy constraints message:
# always
# never
# onerror
- PASSWORD_SHOW_POLICY=never
# Position of password policy constraints message:
# above - the form
# below - the form
- PASSWORD_SHOW_POLICY_POSITION=above
# Who changes the password?
# Also applicable for question/answer save
# user: the user itself
# manager: the above binddn
- WHO_CAN_CHANGE_PASSWORD=user
## Questions/answers
# Use questions/answers?
# true (default)
# false
- QUESTIONS_ENABLED=false
## Mail
# LDAP mail attribute
- LDAP_MAIL_ATTRIBUTE=mail
# Who the email should come from
- MAIL_FROM=Linuxlql@163.com
- MAIL_FROM_NAME=Password Reset
# Notify users anytime their password is changed
- NOTIFY_ON_CHANGE=true
# PHPMailer configuration (see https://github.com/PHPMailer/PHPMailer)
- SMTP_DEBUG=0
- SMTP_HOST=smtp.163.com
- SMTP_AUTH_ON=true
- SMTP_USER=Linuxlql@163.com
- SMTP_PASS=xxxxxx # 这里是邮箱的授权码,经常配置邮箱的你,一定明白我的意思
- SMTP_PORT=25
- SMTP_SECURE_TYPE=tls
- SMTP_AUTOTLS=false
## SMS
# Use sms (NOT WORKING YET)
- USE_SMS=false
# Reset URL (if behind a reverse proxy)
- IS_BEHIND_PROXY=true
# Display help messages
- SHOW_HELP=true
# Language
- LANG=en
# Debug mode
- DEBUG_MODE=false
# Encryption, decryption keyphrase
- SECRETEKEY=secretkey
## CAPTCHA
# Use Google reCAPTCHA (http://www.google.com/recaptcha)
- USE_RECAPTCHA=false
# Go on the site to get public and private key
- RECAPTCHA_PUB_KEY=akjsdnkajnd
- RECAPTCHA_PRIV_KEY=aksdjnakjdnsa
## Default action
# change
# sendtoken
# sendsms
- DEFAULT_ACTION=change
networks:
- proxy-tier
restart: always
networks:
proxy-tier:
external:
name: nginx-proxy
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
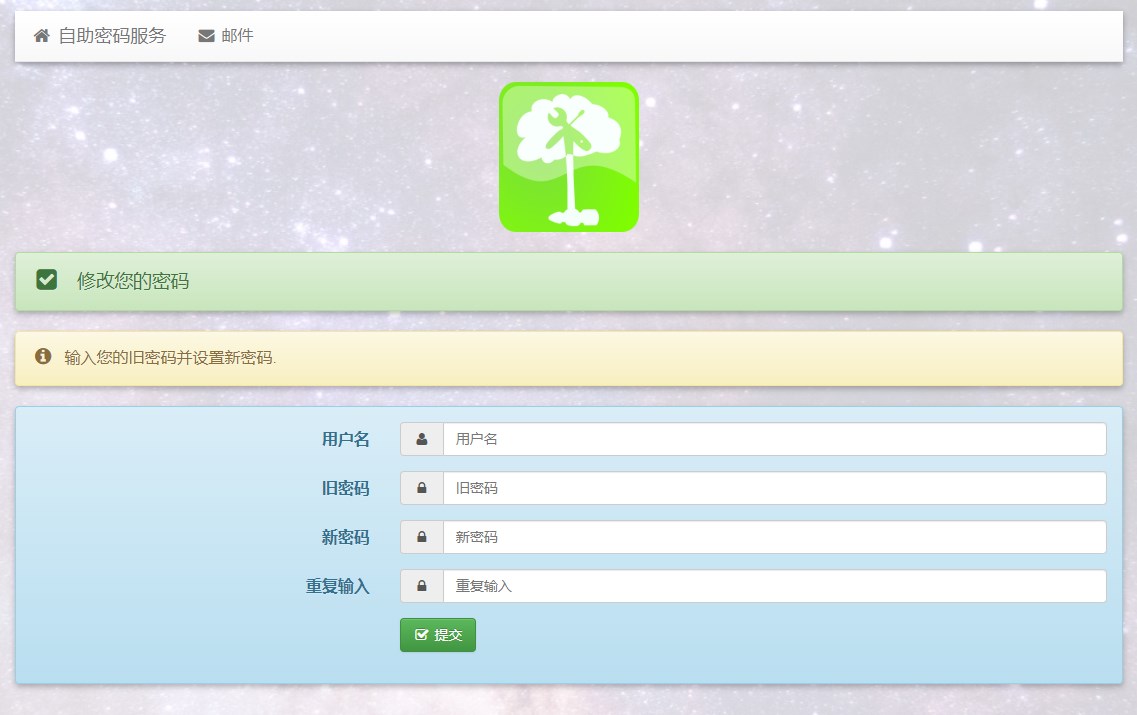
然后直接运行服务即可。访问对应端口可以看到更改密码的页面:


上次更新: 2023/05/29, 22:25:17
 |
|